with azbil
Trivia
- NEW
Targeted attacks

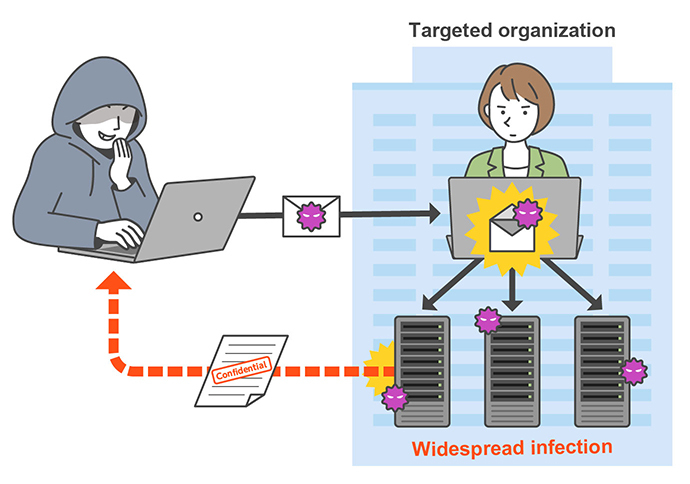
A targeted attack is a cyberattack that targets a specific organization, such as a company or government agency, to steal confidential information or disrupt business. Attackers gain unauthorized access to PCs and servers or use malware to infiltrate them, stealing information and destroying systems.
There are three typical attack methods.
- 1. Unauthorized access They exploit vulnerabilities in cloud services, servers, and VPN*1 devices used by the target organization to infiltrate its systems. In some cases, authentication information is stolen through unauthorized access, and then a legitimate access route is used to gain entry.
- 2. Email attacks Malware*2 is placed in email attachments or links in the body of the email; when the file is opened or the link is accessed, the PC is infected with the malware. The emails may be cleverly disguised to appear natural, such as by listing the name of a real person at the target organization as the sender.
- 3. Website tampering They investigate and narrow down websites frequently used by employees and staff of the target organization; then tamper with and install disguised malware to infect devices that access them.
In 2024, a Japanese crypto asset-related company had its crypto assets*3 stolen by a cyberattack group. The criminal group posed as recruiters on social media and contacted employees of a crypto asset wallet software company*4. A malicious script*5 was sent under the guise of a pre-employment test, and information from employees’ PCs was stolen. Additionally, they impersonated employees and infiltrated unencrypted communication systems. The criminal group stole the crypto assets managed by the company by moving them to a wallet*6 they controlled themselves. Ultimately, the total amount of lost crypto assets reached tens of billions of yen.
To protect an organization from targeted attacks, it is important to thoroughly manage information and to formulate and utilize operational rules. Appropriate security measures are essential for servers, PCs, and networks. It is also important to ensure that all employees are aware of the importance of not opening attachments, or clicking on links or URLs without careful consideration. It is necessary to regularly remind employees to stay vigilant in their day-to-day actions, rather than relying solely on system-based security measures, so that potential threats cannot find any weaknesses to exploit.
-
*1: Virtual Private Network (VPN)
A virtual dedicated line is created on the internet, and communication content is encrypted. A security technology that allows secure external connections to internal systems and prevents information leaks and tampering. -
*2: Malware
Malicious programs that can cause information theft or system destruction. It can be transmitted through email attachments or malicious websites. -
*3: Crypto assets (virtual currencies)
A general term for digital currencies that do not have a central administrator and whose transactions and management are carried out using cryptographic technology. It is used for various purposes, including remittances, payments, and investments. Transactions can be made worldwide via the internet. -
*4: Crypto asset wallet software company
A company that develops and operates software that provides wallet functions for safely storing, sending, receiving, and managing crypto assets (virtual currencies). -
*5: Malicious script
Programs executed on computers or websites that are created with the intent of harming users or systems. -
*6: Wallet
Rather than storing crypto assets themselves, it serves to safely manage the “private keys” used to access assets on the blockchain (a new system for securely recording and managing information).
“10 Major Security Threats” (in Japanese) published by the Information-technology Security Center of the Information-technology Promotion Agency, Japan
- *This article was translated from the Japanese version of the article published on December 10, 2025.

 Related information
Related information

