with azbil
Trivia
Supply Chain Attack

A supply chain includes all the steps involved in producing, shipping, selling, and delivering products or services to consumers, ranging from the procurement of raw materials and components to the final delivery. However, a supply chain attack is a form of cyberattack in which attackers gain access to a target company by exploiting vulnerabilities in related companies or business partners within the supply chain.
Instead of attacking the target company directly, attackers carry out cyberattacks on other companies embedded in the supply chain, using these companies as stepping stones to illegally infiltrate the target company’s network environment. Even if the target company has advanced security measures in place, attackers can reduce the difficulty of infiltration by going through other companies with lower security levels. Additionally, because the attack is disguised as regular business interactions, it is more difficult to detect.
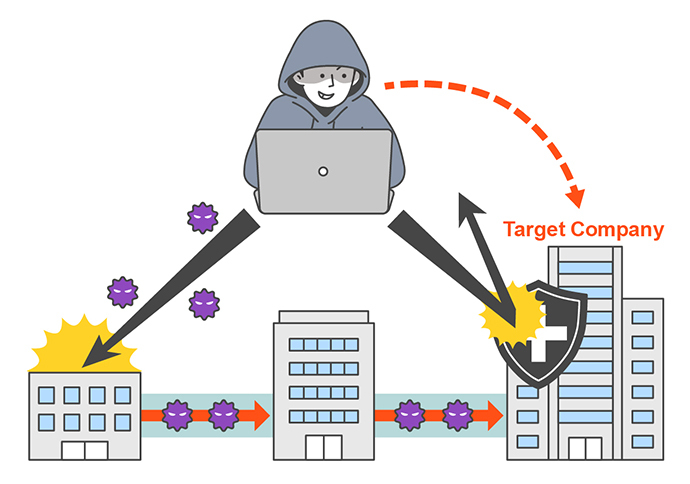
Supply chain attacks can generally be divided into three categories: Business Supply Chain Attacks, Service Supply Chain Attacks, and Software Supply Chain Attacks.
Business Supply Chain Attacks: These attacks exploit security vulnerabilities in subsidiaries or business partners connected to the target company and then gain access to the target company through these connections.
Service Supply Chain Attacks: These attacks infiltrate the target company through service providers, such as Managed Service Providers (MSPs), which are entrusted with managing and operating the target company’s network. Many companies that rely on MSPs may be targeted by ransomware attacks, leading to widespread damage.
Software Supply Chain Attacks: These attacks involve injecting malicious code into software during its manufacturing or distribution process, thereby targeting the target company. The main targets are open source code, system management tools, and essential business applications. If the targeted software is widely used, the damage from the attack can be extensive.
To protect an organization from supply chain attacks, it is essential not only to establish security measures within the organization but also to assess the security levels of related companies, business partners, and subcontractors and enforce security measures across the entire supply chain. The Cybersecurity Management Guidelines issued by the Ministry of Economy, Trade and Industry can prove to be a valuable reference for advancing these measures.
Reference:
Information-technology Promotion Agency, Japan (IPA) Information-technology Security Center “10 Major Security Threats” (in Japanese)
- *This article was translated from the Japanese version of the article published on June 10, 2025.

 Related information
Related information

